Running a Tor relay / node / server on Ubuntu
Updated October 2013: Minor edits.
Right now, for people like me who have access to servers, the single biggest benefit we can provide to society at large is by running a Tor relay. Tor provides anonymity to users of the Internet.
This page is about contributing to the network by running a relay (or server, or node – same thing). If you want to use Internet services anonymously, you probably want the Tor Browser Bundle.
There’s are good official instructions on running a relay.
Install it from the official repository
Edit your sources list: /etc/apt/sources.list
Add the following lines. Substitute ‘raring’ (13.04) with your Ubuntu or Debian version see list:
# Tor
deb http://deb.torproject.org/torproject.org raring main
Add the Tor public key:
gpg --keyserver keys.gnupg.net --recv 886DDD89
gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
Install it:
sudo apt-get update
sudo apt-get install tor tor-arm
Edit the obvious parts of the config file
Edit the config file: /etc/tor/torrc, mainly the This section is just for relays part.
Set the ORPort. Give your relay a nice Nickname. Set Address, ContactInfo, and so on.
RelayBandwidthRate: Throttle it
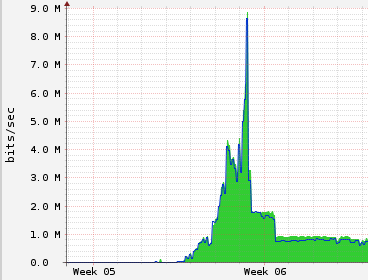
The RelayBandwidthRate and RelayBandwidthBurst settings are very important. The Tor network has many clients (think Tunisia, Egypt, Libya, Anonymous, etc), and they’ll take all the bandwidth you can spare. Here’s what happened to my bandwidth when I left it unthrottled.
After the peak, you can see two steps where I throttled it back gradually.
ExitPolicy: Decide whether you will be an exit relay, and what kind of exit
Traffic in the tor network bounces around between relays, then exits to the real destination. If the Tor user does something nasty to the destination, they will complain to the hosting provider of the exit relay, because it looks like the traffic comes from there.
Your first step should be to just get your relay up and running, without any further reading, so start with no exits:
ExitPolicy reject *:* # no exits allowed
Start it
sudo service tor start
sudo tail -f /var/log/tor/log
Congratulations! You are now, in a small way, helping oppressed people all over the world.
ExitPolicy redux
Exit relays are obviously very important, so you should consider being one. Read these to help you decide:
- So what should I expect if I run an exit relay?
- Tips for running an exit node with minimal harassment
You can decide which ports you allow users to connect to from your exit relay. Obvious ones to block are port 25 (to prevent sending of email spam) and bittorrent ports 6881-7000 (to keep the network fast). Blocking port 80 should cut the bulk of the abuse, but also makes your node less useful, so that’s a tough call.
If you want to dip your toes in the exit waters, be an IRC exit node. IRC is being used by some people in the North African and Middle-Eastern uprisings.
ExitPolicy accept *:6660-6667,reject *:* # allow irc ports but no more
I ran an IRC-only exit for a while with no problems. I’ve recently opened it up a bit more. Here is my current exit policy:
ExitPolicy accept *:22 # ssh
ExitPolicy accept *:465 # smtps (SMTP over SSL)
ExitPolicy accept *:993 # imaps (IMAP over SSL)
ExitPolicy accept *:994 # ircs (IRC over SSL)
ExitPolicy accept *:995 # pop3s (POP3 over SSL)
ExitPolicy accept *:5222 # xmpp
ExitPolicy accept *:6660-6697 # allow irc ports, very widely
ExitPolicy reject *:* # no other exits allowed
Assuming you put correct contact information in your config file, the Tor project will send you an email once your node has been up for a few days, to welcome you to the network.
arm – Watch cool stuff happen
Now that your relay is up, type arm on the command line. Arm is a command line (curses) monitor for your relay.
Happy relaying!